Authority is moving away from observable, precinct-level processes and into centralized, data-driven systems that citizens are not permitted to see, audit, or independently verify in most states.
Part 1 explores how voter databases and election administration are being centralized.
Part 2 explains how modern power operates through data, algorithms, and technofeudal systems.
Protecting voter privacy, preserving local control, and restoring public verification are not competing goals—they are the foundation of legitimate elections.Part 3 of 3: The Question That Ultimately Matters At the end of any serious examination of elections, one question rises above all others:
How do we restore public confidence and democratic legitimacy without sacrificing voter privacy, local control, or the constitutional balance of power?
What follows is not conjecture. It reflects more than two decades of election-integrity work, including firsthand experience examining election systems both inside and outside government. Throughout that work, we have approached elections the same way one approaches a complex puzzle—assembling pieces over time, testing assumptions against evidence, and discarding claims that do not withstand scrutiny.
Along the way, we learned an essential lesson: it is better to understand than to be understood. In elections, that distinction matters. It separates genuine oversight from manipulation—and citizens seeking truth from citizens being guided by belief rather than evidence.
Over the years, the same patterns have repeated themselves. Claims that resist verification. Processes that operate out of public view. Explanations that ask the public to trust, rather than to check.
The controversial Maricopa County audit of the 2020 election made this especially clear. Many well-intentioned people were genuinely searching for answers. Yet they found themselves in an environment shaped by misinformation, opportunism, and false certainty. Access to independently verifiable evidence was limited. Inquiry gave way to groupthink. Belief replaced proof.
For readers familiar with George Orwell’s 1984, this trajectory may feel unsettling—not because votes are being changed, but because power is increasingly concentrated in systems that operate beyond public observation, audit, or challenge.
The shift is quiet.
It does not require altering ballots.
It requires controlling what can be seen, examined, or questioned.
This final section focuses on identifying where that power now resides—and understanding how election outcomes, and public confidence itself, can be shaped without ever touching a single vote.
2. What This Article Is NotIt is important to be clear about what this analysis represents—and what it does not. Examining systems, incentives, and patterns is not an accusation; it is a necessary part of democratic oversight. This article does not assign bad faith to individuals. Its purpose is to distinguish between privacy and verification, authority and evidence, belief and proof.
This is not an attack on Arizona Secretary of State Adrian Fontes or on election officials acting in good faith. In fact, Secretary Fontes has taken a principled and constitutionally grounded position in resisting federal efforts to centralize states’ voter data into one centralized federal database — efforts that would shift sensitive election infrastructure and data, including social security numbers and other personal identifying information, into one opaque federal system.
Where this article draws a careful—but crucial—distinction is here:Protecting voter privacy and resisting federal data aggregation is not the same thing as opposing public election verification.
These positions are not in tension unless privacy is mistakenly used to block verification.
To underscore that point, Secretary of State Fontes has publicly supported “radical transparency” measures that would make election outcomes more verifiable through public records—without compromising voter identity. His testimony in support of ballot-image transparency during consideration of HB 2560 is linked here. That legislation passed with bipartisan support before being vetoed by Arizona’s Governor.
Title: Could Ballot Images Loosen the Grip of Disinformation?3. Understanding Ballot Anonymity: Why Your Ballot Is SafeAuthor: Steven Rosenfeld - Publication: Washington Monthly
Date: April 4, 2023
Summary: This article discusses Arizona’s efforts—including strong backing from Secretary of State Adrian Fontes—to increase election transparency by making ballot images and voter data publicly accessible as a tool against election disinformation.
A lot of voters think their name is secretly attached to their ballot — especially because vote-by-mail tracking sends messages like “We received your ballot” and “Your ballot has been counted.” What most people don’t realize is that those messages refer to the envelope, not the ballot.
Once a ballot leaves your hand at a vote center, or once elections staff remove it from the mail-return envelope, there is nothing on that ballot that ties it to you. No barcode. No number. No digital tag. Nothing.
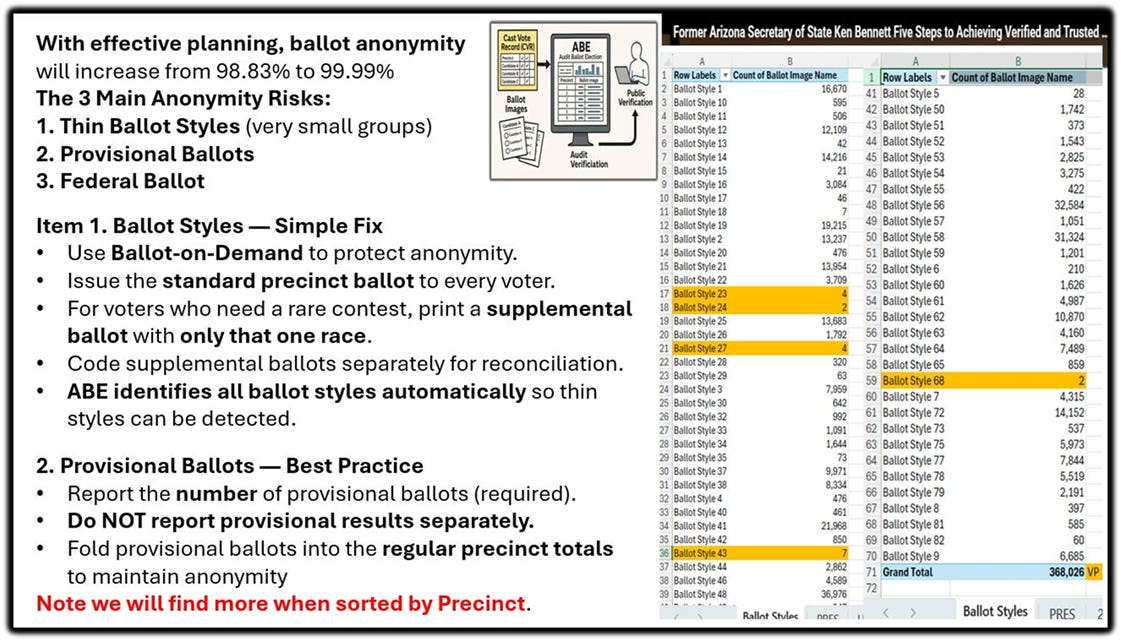
Independent studies, including a major report from Maricopa County, show that 99.83% of ballots are already completely anonymous, and with simple improvements — like using ballot-on-demand printers to issue supplemental ballots for rare ballot styles — counties can raise protection to 99.98% or higher.
Ballot anonymity is not the problem.
The problem is that most people don’t know how anonymous their ballot truly is — and no one has ever explained it plainly.
Video: Ken Bennett explains the 1912 string in this video clip from Cochise County Dec 4, 2025 Study Session
4. Privacy and Verification Are Not the Same Thing(Posted by John Brakey)
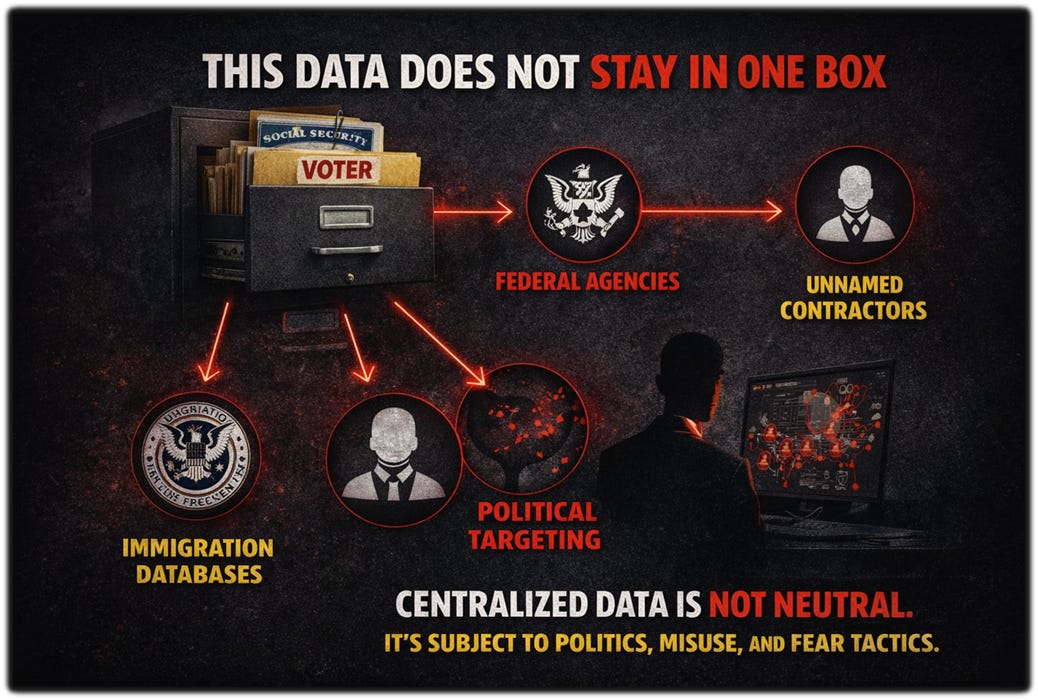
Efforts by the federal government to expand its access to unredacted voter databases and centralize state databases at the federal level represent a top-down expansion of federal power and intrusion into states’ affairs, which federal officials are attempting to justify with expressed concerns over voter-list maintenance and fraud detection.
Many state officials—across parties—have rightly questioned both the necessity and transparency of that approach, along with fears that a federally centralized voter list could be manipulated to swing federal elections.
At the same time, bottom-up verification tools that allow citizens to independently confirm election outcomes—without exposing voter identities and without centralizing control—have often been misunderstood, delayed, or dismissed.
This confusion has had real consequences.
When privacy concerns are used—intentionally or not—as a reason to block verification, elections drift away from evidence and toward authority. Citizens are told to trust outcomes they are not allowed to examine. And trust, once broken, does not return on command.
A Real-World Example: When States Say No to Federal Voter DatabasesWhat this shift looks like in practice is no longer theoretical. It is happening now, in real time, and state election officials are being forced to choose whether to comply—or resist.
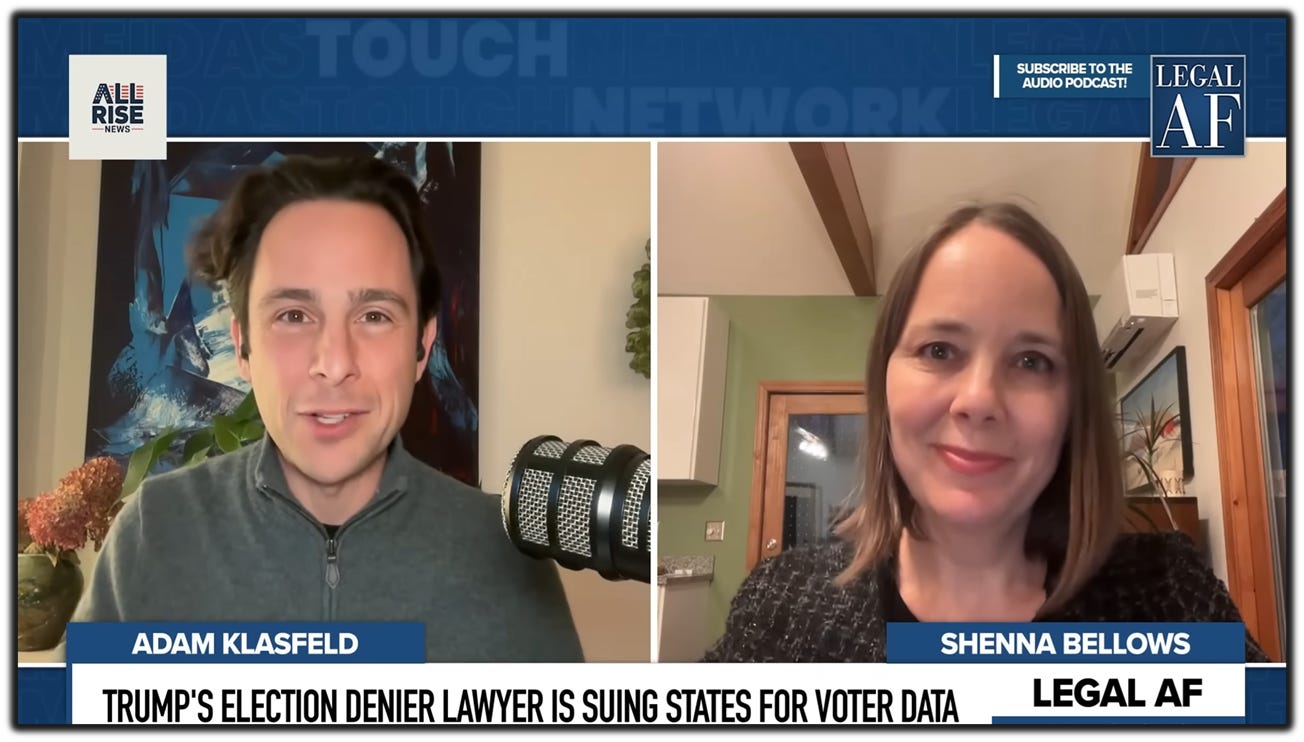
A clear example comes from Maine, where Shenna Bellows, the state’s Secretary of State and former head of the ACLU of Maine, has publicly described how the U.S. Department of Justice demanded her state’s entire voter database—voter history, party affiliation, social security numbers, and other personal identifying information.
In a short interview, Maine’s SOS Bellows described the effort bluntly:Bellows refused. Her explanation was straightforward and constitutional: elections are administered by states, not the federal government, and centralized voter files pose serious risks to privacy, security, and democratic participation.
“They’re trying to build a giant voter file. ‘Purge machine’ is a good description of that.”
She warned that consolidating voter data at the federal level would create “a one-stop shop for identity thieves” and could be used to justify large-scale voter purges—particularly in states governed by political opponents.
Importantly, Bellows emphasized that resistance has been bipartisan. More than two dozen states have refused similar demands, while lawsuits have been filed exclusively against states with Democratic governors. Whether one agrees with Bellows politically or not, her account underscores a critical point: protecting voter privacy and resisting federal data aggregation is not the same thing as opposing transparency or public verification of election results.
The danger lies not in scrutiny, but in consolidation—when oversight flows upward into systems the public cannot see, audit, or independently verify.
SOS Bellows emphasizes that this is not an isolated incident. She reports that:27 states have refused to comply
14 states have been sued, all with Democratic governors
Resistance is bipartisan
The DOJ is citing the National Voter Registration Act—but, in her words, has “turned it completely on its head”
She calls the effort what it is: an unprecedented federal power grab, occurring just ahead of critical midterm elections.
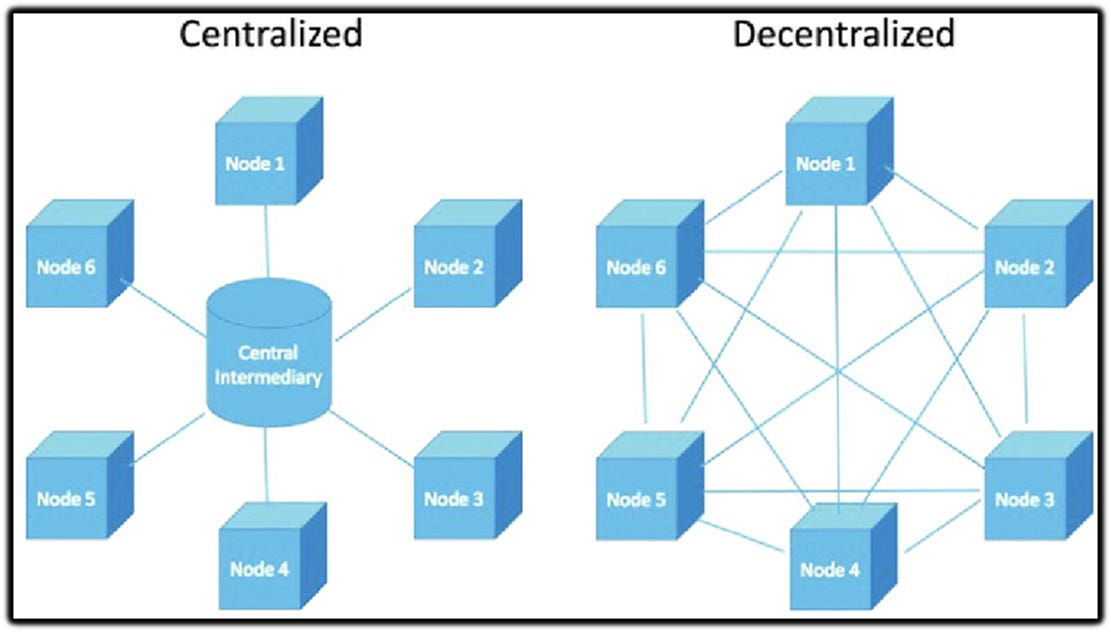
5. Where Election Power Actually Lives Now This tension points to a deeper structural problem.Modern election power no longer resides primarily in ballots or counting rooms.
For people unfamiliar with election systems, this is the key insight:It lives in databases, spreadsheets, macros, and administrative chokepoints—systems that quietly determine who is counted, who is flagged, and how results are constructed long before the public ever sees a final number.
You do not have to change a single vote to change an election outcome. You only need control over the data pipeline.
6. The Inventory System Problem (Why This Is Not Abstract)Twenty-one years ago, when I (John Brakey) first encountered electronic voting systems, something immediately stood out: it looked like an inventory system.
That made more sense once you understood the companies and software roots behind early electronic voting. Some early systems were adapted from commercial software designed to track parts, screws, and equipment. The logic was simple:
But people are not parts. And elections are not inventory.
Yet the underlying architecture often treats voters as categorized units—by party, by ballot style, by eligibility flag—processed through databases that can be altered, reordered, or summarized before anyone outside the system ever sees them.
And if results are “committed” before public verification occurs, everything downstream can be made to align with the announced outcome.
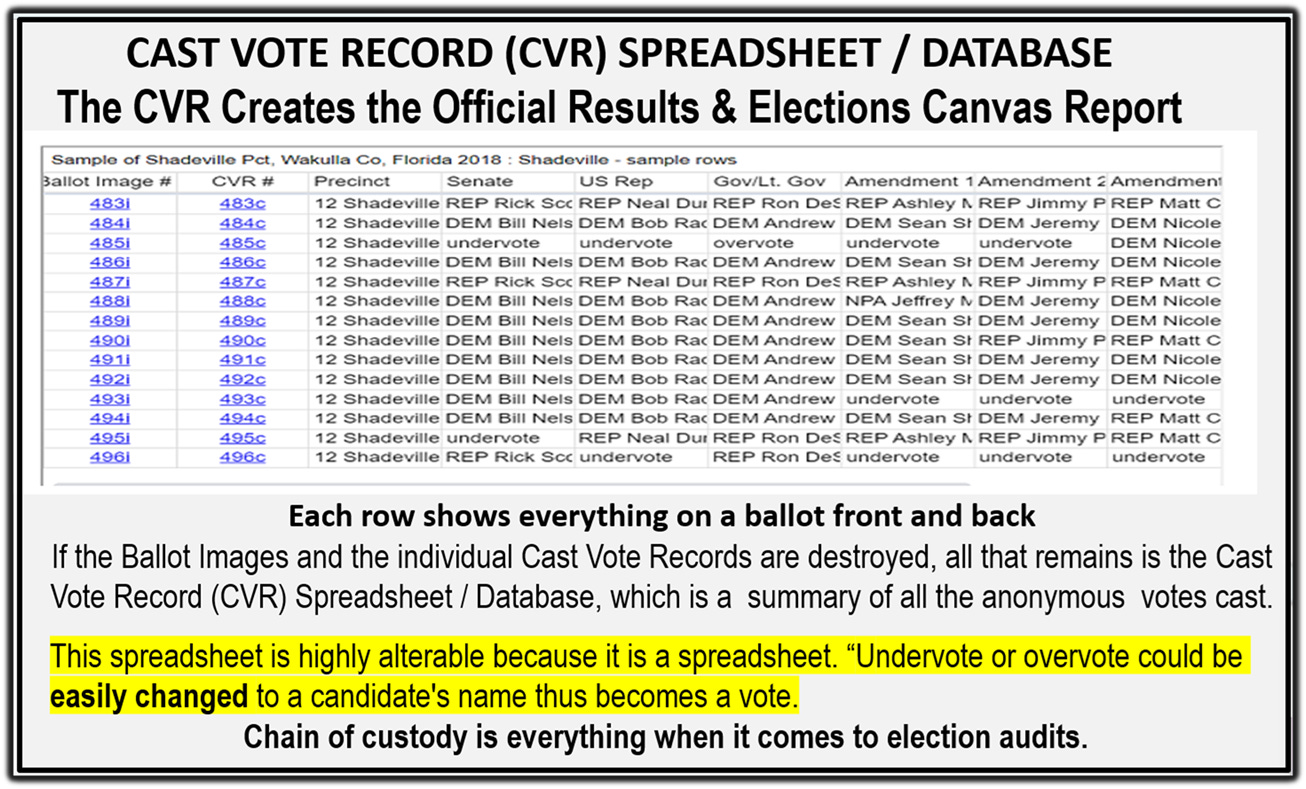
Here Is Why This Matters Now Because beneath every modern election system lies a single, quiet truth:The voter CVR database is power.
Not the ballot box. Not campaign ads. Not even Election Day itself.
At its core, the database is just a spreadsheet. Without ballot images, its meaning depends entirely on who controls it—and how.
7. Why Ballot Images Change EverythingThat reality is not unique to elections. It reflects a broader shift in how power is exercised across modern governance.
This is why access to ballot images is not a technical preference.
It is a democratic necessity.
Ballot images anchor digital records to physical evidence. They turn abstract databases back into observable reality.
Without images, a Cast Vote Record (CVR) is just a spreadsheet.
With images, it becomes verifiable evidence.
That difference is everything.
8. A Simple Path Forward: Auditable Ballot Examination (ABE)Ken Bennett:
“This is where Auditable Ballot Examination (ABE) enters—not as a theory, but as a practical response to known vulnerabilities. ABE is an election verification system offered by AUDIT Elections USA to election officials and to the public, at no cost beyond access to an adequate computer and standard spreadsheet software such as Microsoft Excel.”
Ballot images
Cast Vote Records (CVRs)
Precinct-level reports
Expose voter identities
Centralize authority
Require federal control
Change how people vote
Public verification.
99.95% of voter choices cannot be publicly revealed
Even if all CVRs were released, 99.83% of voters remain fully anonymous
Thin ballot styles (unique, customized ballots issued to one or two voters in a precinct)
Thin federal-only ballots (rare ballots that stand out)
Provisional ballots (small counts, often flagged distinctly)
Thin ballot styles: Issue a standard precinct ballot plus a one-contest supplemental ballot when needed.
Federal-only ballots: Duplicate voter-marked choices onto a standard ballot shell, leaving unused contests blank.
Provisional ballots: Mix accepted provisionals into the regular precinct batch before imaging or tabulation.
10. How ABE Supports These Protections ABE immediately identifies thin categories by precinct. When such a ballot appears, staff can:These steps preserve the original ballot as legal evidence, require no statutory changes, protect voter privacy, and increase anonymity while expanding transparency.
Duplicate the voter-marked portion onto a standard precinct ballot (omitting unique contests), and
When the unique contest must be preserved, produce a one-contest supplemental ballot
This preserves anonymity while maintaining the evidentiary integrity of the original ballot—the gold standard for public verification.
11. From Elections to Governance: The Palantir Warning.(By John Brakey)
To understand where centralized election data systems can lead, it helps to look beyond elections to companies already shaping how governments collect, integrate, and act on data at scale.
One of the most influential is Palantir Technologies, co-founded by Peter Thiel. Palantir’s software is designed to fuse vast datasets across agencies, creating powerful analytical environments used by defense, intelligence, law enforcement, and immigration authorities.
Supporters describe this as efficiency. Critics describe it as a shift in governance—away from human judgment and public accountability and toward opaque, algorithmic decision-making that citizens cannot see or challenge.
Palantir’s record has raised persistent concerns among civil-liberties advocates. Its tools have been linked to predictive policing programs conducted without public oversight, large-scale immigration enforcement systems that aggregate personal data for targeting and deportation, and military applications that accelerate algorithm-assisted warfare.
This is not an argument about one company or one administration. It is a warning about architecture.European officials and courts have questioned whether using U.S.-based data platforms like Palantir for sensitive government functions creates data-sovereignty risks, highlighting broader concerns about who ultimately controls critical state databases.
(The Guardian) Mon 22 Dec 2025 06.26 ESTPhotograph: Lucy North/PA
When critical civic functions depend on centralized data systems that operate beyond public verification, power quietly shifts away from citizens.
Elections, like immigration or policing, become matters of database authority rather than observable evidence.
12. “I Worked At Palantir: The Tech Company Reshaping Reality”Views 3,154,873 — Apr 17, 2025 - (Posted by John Brakey)
A former Palantir employee is sounding the alarm. The tech company, founded by Peter Thiel, claims they can revolutionize government systems with their AI-powered software. They’ve been hired by the Department of Defense, the FBI, ICE, and even Wendy’s.
13. The New Chokepoint of DemocracyIn earlier eras, controlling elections meant controlling ballots, polling places, or counting rooms.
Today, elections can be decided long before ballots are cast—inside data systems that determine:Who is registered
Who is flagged
Who is removed
Who must “prove” eligibility
Mission creep
Selective enforcement
Political leverage
It does not require bad intentions. It does not require corruption.
Once officials can quietly say, “The database shows you’re ineligible,” the burden shifts from the state proving its case to the citizen proving their worthiness.
15. This Is Not About Fraud. It’s About Leverage.That is not democratic governance. That is administrative power.
So why the urgency to centralize voter data?
And once a system becomes the arbiter of reality, those who control it gain power over outcomes of:Who participates
Who is discouraged
Who trusts the process
American democracy was never designed to run on trust alone.
It was designed to run on:Checks and balances
Observable processes
Chain of custody
Public verification
That principle has been quietly abandoned.
Citizens are now told:Trust the database.
Trust the algorithm.
Trust the authority.
Trust the experts.
17. Why Transparency Is the AntidoteBut trust without verification is submission, not consent.
This is where Auditable Ballot Examination (ABE) matters:
ABE does not ask citizens to trust anyone.
It does not centralize authority.
It does not expose voter identities.
It allows the public to verify election outcomes using evidence
Ballot images
Cast Vote Records
Precinct-level reconstruction
No secrets
No faith required
That single shift—from trust to verification—changes everything.18. What Real Power Reclamation Looks Like
Democracy does not survive because people are virtuous.
It survives because systems are verifiable.
When citizens can:See how votes are counted
Check outcomes independently
Confirm results without intermediaries
then power flows upward, not downward.
19. The Courage Requirement.When citizens are told to trust databases they cannot examine, democracy becomes performative.
None of this works without the courage to stand up.
Courage to ask:Who controls the data?
Who benefits from opacity?
Why is verification resisted?
“I don’t want reassurance. I want evidence.”
Questioning power is not disloyalty.
It is civic responsibility.
There is a word I (John Brakey) have wrestled with for a long time: omniscience—the idea of something all-knowing, god-like, a constructed authority that sees everything.
Looking back over more than forty years as an activist, I can see now that what we once called “Big Brother” was never just a metaphor. It was a destination. And today, the tools to build it are finally here.
What troubles me most, after decades of work in election transparency, is not any single technology or agency—but the trajectory.
For years, “Big Brother” was treated as a warning. A dystopian exaggeration. Something safely hypothetical. What recent efforts to merge and centralize government data reveal is something far more concrete:Omniscience is no longer a metaphor. It is becoming an architecture.
The push to eliminate “information silos” and merge databases—often framed as efficiency—creates the conditions for systems that can see everything, remember everything, and correlate everything. When paired with modern artificial intelligence, centralized data does not merely record the past; it begins to model, predict, and target the future.
Omniscience has long been defined as perfect knowledge—complete awareness without the need to learn, revise, or explain. Nothing is hidden. Nothing can be questioned.
The Privacy Act of 1974 was written in the shadow of Watergate and COINTELPRO, when Congress recognized a fundamental democratic truth:This is not about malice.
It is about power without friction.
there must be limits on what the government can know about its citizens.
Efforts to create massive, centralized data systems press directly against that boundary. Even if pursued legally, even if justified procedurally, the result is the same: manufactured omniscience, achieved not by tyranny, but by administrative convenience.
History teaches us that the most dangerous systems are rarely built with evil intent. They are built with good intentions—and no exit ramps.
Powerful actors—governments, institutions, corporations, and financiers—are racing to build systems of artificial omniscience. The logic is simple:the more information you feed the machine, the more it knows.
Instant memory.
Perfect recall.
Systems that never forget.
That should give us pause—not because technology is evil, but because history shows us what happens when authority claims to know everything.
We have seen this kind of power before. It has appeared in many forms—empires, ideologies, cults, and belief systems—especially when certainty replaces inquiry.
Believe this or be punished.
Fall out of line and suffer the consequences.
Ken Bennett and John Brakey interviewed during the 2021 Maricopa audit.
For me (John Brakey), this is not theoretical.” It is personal.When truth is presented as absolute and unchallengeable, force becomes unnecessary. Obedience follows on its own.
I ran away from home one month after turning fifteen because I was living inside an Armageddon-oriented belief cult that taught me life was short, judgment was imminent, and certainty was everything. That way of thinking shaped how I saw the world—and even now, I still carry traces of it.
I think about that when I remember raising three baby ducklings as a child. Everywhere I went, they followed me. They believed I was their mother. That kind of imprinting—of trust and dependence—doesn’t require malice. It only requires authority and proximity.
Therapy later taught me how to separate fear from analysis, belief from evidence, and reaction from reflection. I don’t raise these concerns lightly, and I don’t raise them from panic. I raise them because I have learned, firsthand, how easily certainty can replace understanding.
Over the last two decades, I have watched something take shape that few people were willing to name. What we once feared as “Big Brother” did not arrive wearing a uniform or carrying a weapon.
It arrived quietly—wrapped in data, algorithms, and promises of efficiency.
Today, systems are being built that aspire to see everything, remember everything, and decide without empathy—or accountability.
This is not wisdom.
It is not democracy.
It is a false god made of data—one that demands trust while resisting scrutiny.
History is clear: whenever authority claims to be all-knowing, the result is not order. It is abuse.
Democracy survives only when power can be questioned, evidence can be examined, and citizens can see for themselves.
Voting must remain secret.
But counting—like power itself—must never be hidden.
Every democratic republic eventually reaches the same fork in the road:
Centralized control + managed trust, or
Distributed verification + informed citizens
There is no stable third option.
The good news is this:One citizen still matters.
Not by shouting. Not by choosing sides.
But by insisting on transparency.
Voting must remain secret.
Counting must be public.
The people—not databases—must remain sovereign.
The central risk is not technology itself, but the loss of democratic transparency and citizen verification in systems that increasingly govern reality.
Let’s work together to create A Better Election—for everyone with programs like ABE.Ken Bennett, Chairperson, AUDIT-USA kbazsos@gmail.com | (928) 445-2949
John R. Brakey, Executive Director, AUDIT-USA Johnbrakey@gmail.com | (520) 339-2696
Executive Director, AUDIT Elections USA
Co-Developer of the ABE Hybrid Verification System
Election Transparency Investigator, Educator & Reform Advocate
“Without verification, trust cannot be established.” — Bennett & Brakey
AUDIT USA is a 501(c)(3) organization. Your donations are tax-deductible!
Send donation check to:
AUDIT USA P.O. Box 26361
Tucson, AZ85726
We appreciate donations of any size.
ConclusionThe document concludes that election integrity depends on transparency, public oversight, and verifiable audits. ABE offers a practical tool to restore these principles by linking ballot images to CVRs for accessible, citizen-led verification. The report underscores that trust in elections cannot be demanded but must be earned through openness and accountability, echoing the principle: “Trust, but verify”
Thanks for reading John’s Substack! Subscribe for free to receive new posts and support my work.
Trump’s DOJ offers states confidential deal to remove voters flagged by feds Justice Department attorneys says 11 states have shown a willingness to stop residents from voting at DOJ’s request.By: Jonathan Shorman-December 18, 2025 3:29 pm
National Elon Musk’s DOGE is feeding sensitive federal data into AI to target cutsUpdated February 6, 2025: At the Education Department, the tech billionaire’s team has turned to artificial intelligence to hunt for potential spending cuts --- part of a broader plan to deploy the technology across the federal government. https://www.washingtonpost.com/nation/2025/02/06/elon-musk-doge-ai-department-education/?utm_source=chatgpt.com